The development of the IoT market will rely on technology advances in the semiconductor component industry and the software industry. McKinsey estimates that 30 Billion devices will be connected by 2020. Microelectro-mechanical-systems (MEMS) technology will play a significant role in enabling Internet of Things application. MEMS helps to overcome the challenges of integration, power, and cost.
The economic value of connecting sensors and devices brings tremendous value because data can now be processed in real time. Information can now be disseminated across a much wider industry eco-system to manage product life cycles, perform scheduled maintenance, and manage the supply chain. Other obvious benefits include applying predictive analysis to allow managers to make much more timely informed business decisions.
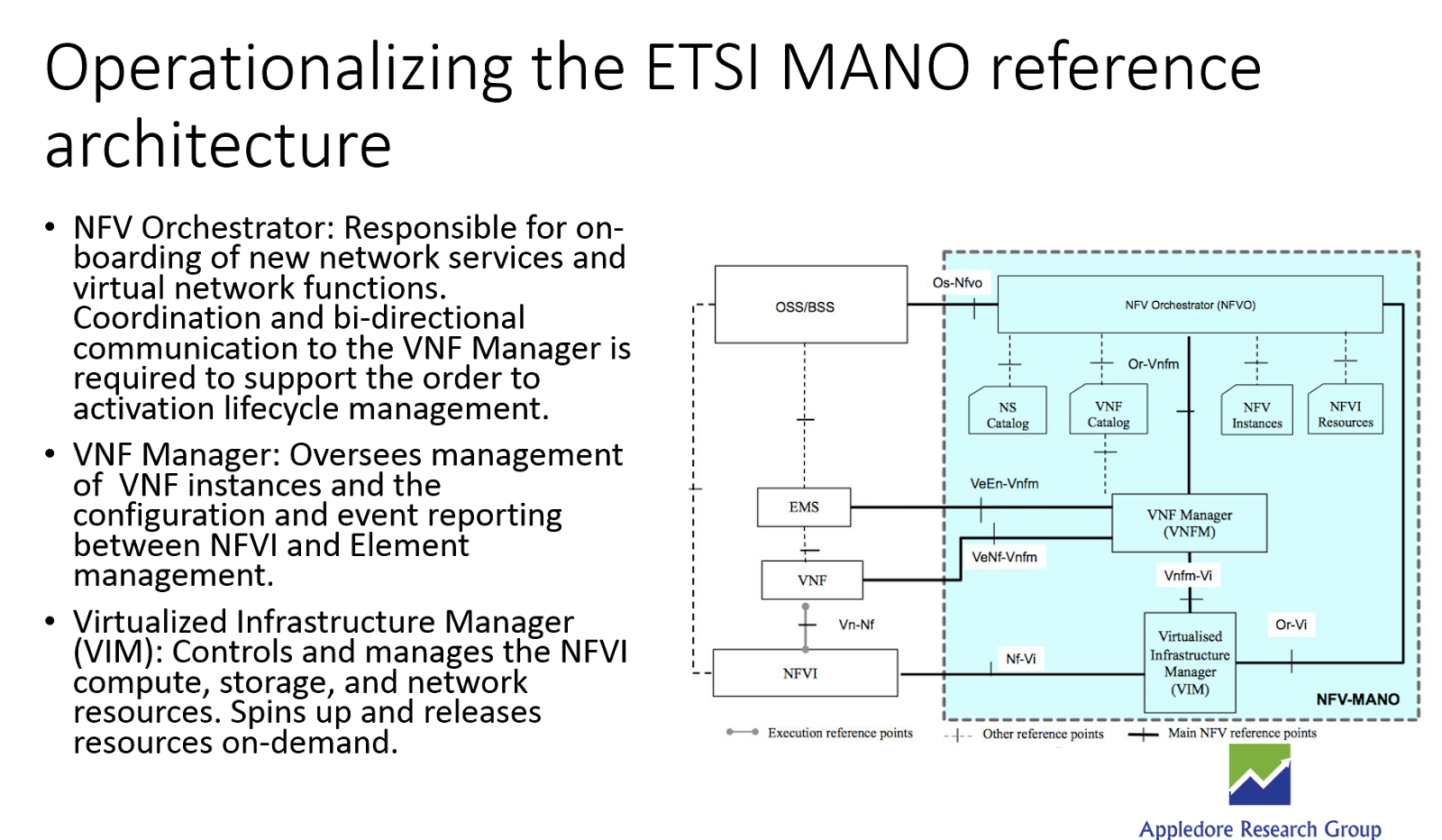
Most of the value derived from IoT systems will come from the IoT Application Platform. The IoT Application Platform will enable developers, business partners, and customers to build, deploy, and share information across the expanded industry eco-system (see my previous blog “IoT Service Enablement Platform Role in 2020).
The commercial software market is fragmented with software suppliers providing strong support in some areas of the IoT application platform and lacking functionality in other areas. The IoT Application Platform is responsible for managing connected devices, providing API gateways to existing systems for legacy data exchange, data analytics and secure data storage.
The three most important considerations in building or buying an IoT Application Platform is to make sure it supports:
1) Open standards
2) Hybrid Cloud
3) Security
Many industry standards are emerging in the IoT space. This includes everything from network communication protocols to data models. oneM2M just issued its Release 1 global standards Feb 4 2015. The IEEE and ETSI are both active in developing low throughput network protocols and interfaces. Some of the open source groups include Open Interconnect Consortium, AllSeen Alliance, and Industrial Internet Consortium. The objectives are intended to define a common communications framework based on industry standard technologies.
Developers and software suppliers of IoT Application Platforms should promote support of heterogeneous IoT devices to communicate and leverage common software applications and embrace standards as the market matures. The dynamics of competing interest and lack of standards will be a long term process over the next decade, especially with competing consortiums.
A hybrid cloud environment enables industries to scale up rapidly to support billions of connected devices. It also facilitates agile development with fast deployment timeframes. The hybrid cloud will become more mainstream with business critical applications as the infrastructure becomes more hardened to security vulnerabilities. I use the term hybrid cloud because I expect that Enterprise customers will bridge their private clouds with public clouds which may be provided by partners, CSPs, government agencies and other companies in the ecosystem depending on the IoT applications.
The cloud provides the necessary scaling to support the requirements of Fortune 500 industries such as shipping and manufacturing which rely on a global communication infrastructure. Because no CSP can claim to operate a global network, the business models will require partnerships that are able to support the connected platform subsystem.
The IoT Application Platform could be installed on premise or hosted as a Software as a Service (SaaS). The advantage to a SaaS model is that companies looking to stand up an IoT business can deploy services quickly without expensive upfront capital cost and long integration cycles. Most commercial IoT platforms provide the management tools, APIs, and an integration framework to rapidly build new applications and integrate into existing software systems.
Security is paramount for both industrial and consumer industry verticals. As part of an overall secure IoT application platform all access to the system must be centrally controlled and provide password encryption and authentication. The system must also protect against malicious control of the devices and network infrastructure. Finally access to the data must be secured and controls must be applied to the level of access granted to users based on their role. This is important for a diverse system of suppliers, partners, and end user customers.
The security provided must consider legacy based systems such as Industrial Control Systems (ICS). Before IoT there was ICS. Critical infrastructures, such as electricity generation plants, transportation systems, oil refineries, chemical factories and manufacturing facilities have deployed sensors and management systems since the era of the mainframe. ICS are command and control networks and systems designed to support industrial processes. The largest subgroup of ICS is SCADA (Supervisory Control and Data Acquisition) systems. These systems were not designed for the security threats posed by today’s hackers and internet DDOS and viruses. The evolution of these systems is important to better understand the vulnerability to computer network-based attacks. The reliable function of SCADA systems in our modern infrastructure is critical to public health and safety. As such, attacks on these systems may directly or indirectly threaten public health and safety.
In an attempt to isolate the three areas that will act as the biggest challenges to IoT adoption, I neglected to point out other capabilities of the IoT Application Platform that are important considerations. Certainly data streaming and the use of real time analytics is an important component to make informed business decisions. Development tools that support device gateway support are useful for extending management and control. Many commercial solutions also support a non-programmatic graphical tools to configure scripts, alarms, business logic, and custom rules for the devices and sensors deployed or about to be put into service. I will be profiling IoT Application Platform commercial solutions in future research reports.